Associate an API Gateway
For us to be able to use request signing and IAM-based fine-grained access control, we’ll first need to associate an IAM policy that provides permissions to invoke API operations for your API Gateway deployment. For further details, you can review controlling access to an API with IAM permissions documentation.
High-Level Instructions
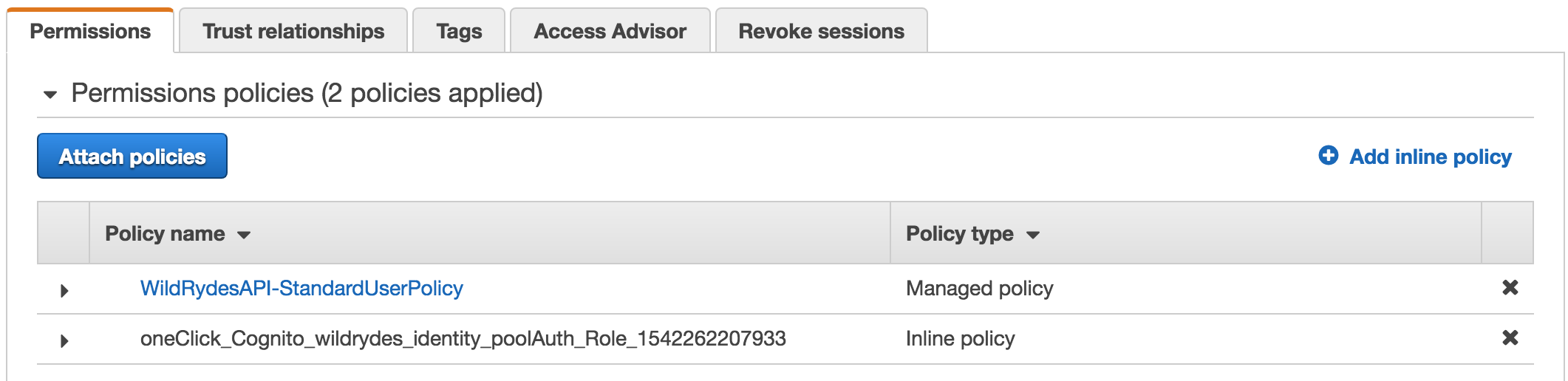
In the IAM console, associate the WildRydesAPI-StandardUserPolicy with your Cognito Identity Pool’s authenticated user role to provide all authenticated users access to invoke operations the /ride path.
-
Go the AWS Management Console, click Services then select IAM under Security, Identity, and Compliance.
-
Choose Policies.
-
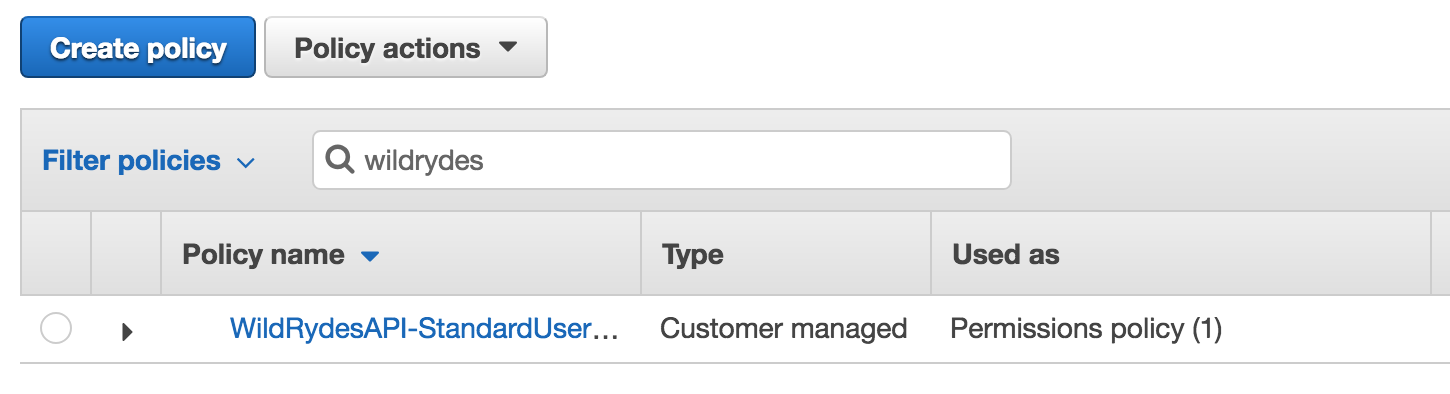
Search for WildRydes to see the WildRydesAPI-StandardUserPolicy which was created by the Serverless Backed CloudFormation template.
-
Click the WildRydesAPI-StandardUserPolicy policy name.
-
Review the policy which was created by CloudFormation to authorize requests to your API Gateway deployment.
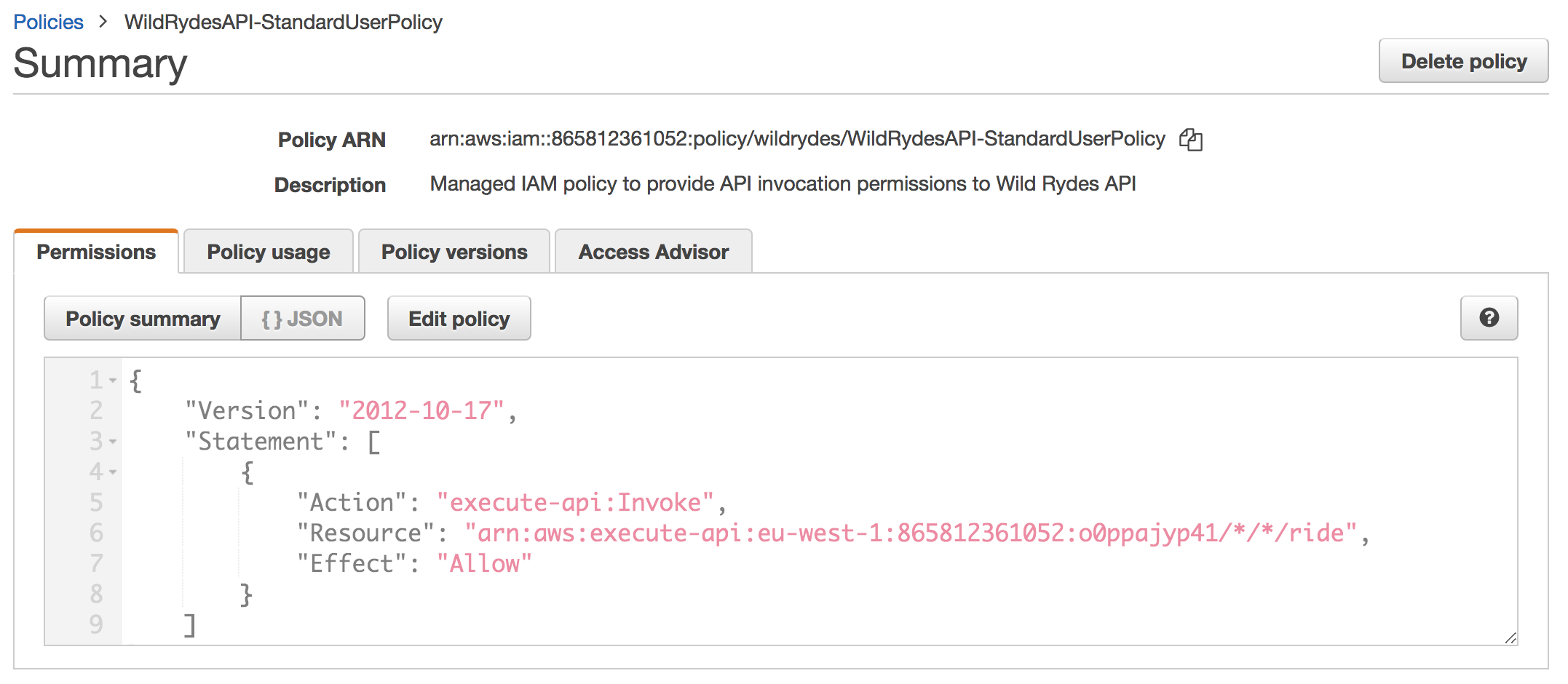
This policy allows access to invoke any method on the /ride path for any API stage of your API gateway backend. For more details about authoring IAM policies for API Gateway, visit the controlling access to an API with IAM permissions documentation.
-
Choose Roles.
-
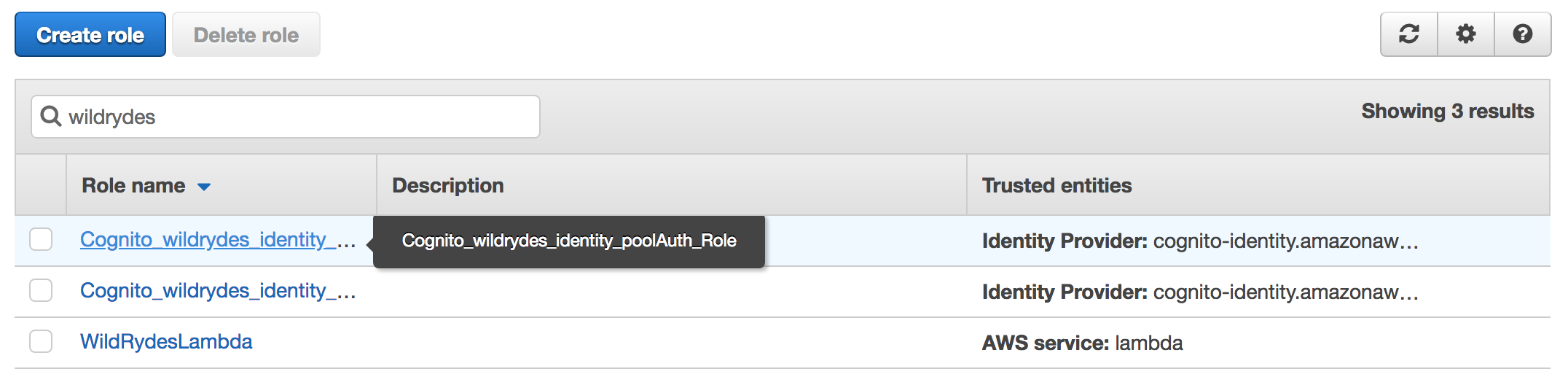
Search for WildRydes to find the two roles which were created by Cognito Identity Pools when you created the Identity Pool in module one. Should you not be able to find the roles here, you can alternatively go to the Cognito Federated Identities console, find the correct identity pool, then click Edit Identity Pool in the top-right corner to see the roles listed. Each identity pool has both an Unauthenticated user role and an Authenticated user role.
-
Once you have found the names of the roles, go back to the IAM console and select the Auth role for your authenticated users.
If the full name of the role is hidden from view due to column width, you can hover over the partially visible name of the role to see the full name of the role as a tool tip.
-
Choose Attach policies.
-
Search for
WildRydesand check the box next to the policy named WildRydesAPI-StandardUserPolicy.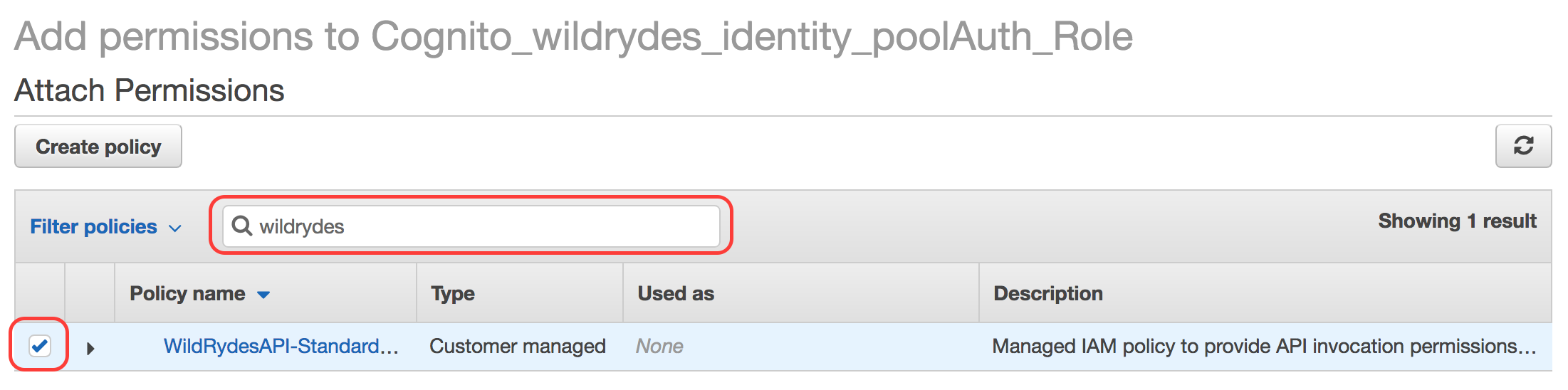
-
Choose Attach policy.
-
You should now see the WildRydesAPI-StandardUserPolicy policy associated with your Cognito IAM auth role.